
Hidden Keys
Hidden encryption keys are written into each tag during the encoding process.
These keys are also stored on the ixkio platform.
Leverage the power of authentication tags using your existing platform.
Authentication NFC tags feature advanced NFC chips designed to safeguard against unauthorised duplication.
They are compatible with all NFC enabled phones and require no special app to be downloaded by the user.
Ixkio offers comprehensive support for authentication tags including key storage, unique code authentication, rule creation based on outcomes, and securing the link to your website's landing page.

Hidden encryption keys are written into each tag during the encoding process.
These keys are also stored on the ixkio platform.
Tags generate a unique 'auth' code using the key on each and every scan.
This auth code is dynamically added to the scan URL.
The 'auth' code is verified by ixkio using the same tag key.
This checks that the tag is genuine and hasn't been copied.
Authentication was built into the ixkio platform from the start.
Combine with Rules, Assignment, CodeLink, Subtags and many other ixkio features
to create your own system.
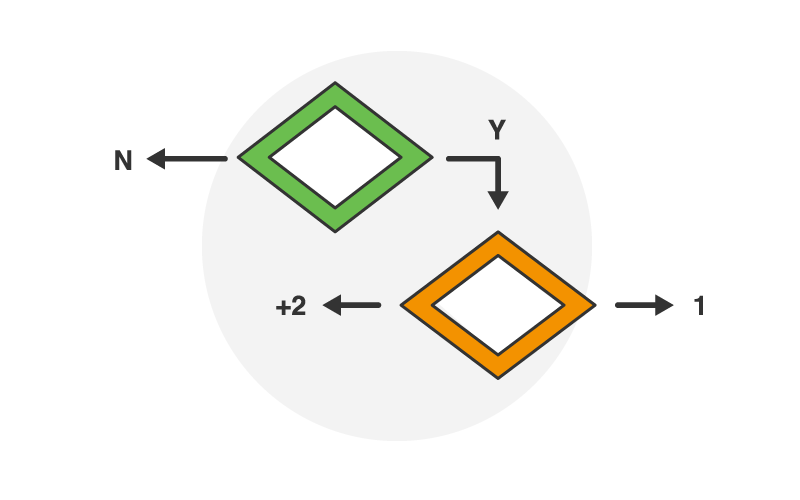
Create rules to redirect users based on authentication status.
Restrict digital content based on physical products.
Manage and control authentication tags like standard tags.
Use ixkio's powerful tag Assignment systems to deploy pre-encoded tags quickly.
Protect the physical to digital from unauthorised redirect landing page access.
Activate CodeLink effortlessly. Use our Shopify App or embed a single line of code in your page.
Dynamically include Tag Code data into your redirect or API response.
Create dynamic URLs for dynamic page content or performance tracking.
Using authentication NFC tags has never been easier - whatever your project.
.
Tag scans are authenticated by ixkio with users instantly redirected to pages on your current website.
Easy Start
Start integrating tags, decide content later. Use your existing website.
Dynamic Links
Update destination tag URLs remotely via ixkio as often as you need.
Full Control
Manage tags using rules, folders, tag groups and more.
CodeLink Support
Add a simple javascript snippet to your landing pages to prevent direct hits.
Tag scans are authenticated by ixkio with users instantly redirected to pages on your current website.
Easy Start
Start integrating tags, decide content later. Use your existing website.
Dynamic Links
Update destination tag URLs remotely via ixkio as often as you need.
Full Control
Manage tags using rules, folders, tag groups and more.
CodeLink Support
Add a simple javascript snippet to your landing pages to prevent direct hits.